
On Tuesday, May 16th Lloyd had the privilege to co-host our first Lunch & Learn of the year with our partner, iland, a premiere cloud storage and Disaster Recovery as a Service (DRaaS) firm. The audience consisted of a group of 26 individuals from the Lloyd community including potential and existing Lloyd clients, Lloydians, and our team at iland Zee Humayun and Curtis Johnson. Dave Curley, Principal Consultant for Lloyd’s Financial Services firms, kicked off the event with details on why Lloyd chose disaster recovery and security as our main topics, which is a result of client feedback from our survey completed in 2016. 68% of respondents identified Disaster Recovery as a priority objective, and 81% listed security.
The Lunch & Learn is a result of Lloyd’s 2017 dedication to strengthening our relationships with our existing community through frequent and effective educational content. We’re excited to host more events this year and welcome any feedback or thoughts for future topics so we can continue to gear the conversation towards the needs of our community. The backbone of our communication plan is our core values: to be human, be accountable, be better.
.png?width=640&name=Untitled%20design%20(1).png)
Key Points from Our Speakers
Zee and Curtis from iland reviewed their DRaaS platform, which utilizes Zerto’s backend technologies to provide an instantaneous failover environment for essential data. Attendees were given an overview of the Gartner and Forrester named “leader” organization, and some key features of their disaster recovery services including automated continuous data protection, 7 day journaling, and non-disruptive DR testing to help satisfy compliance requirements.

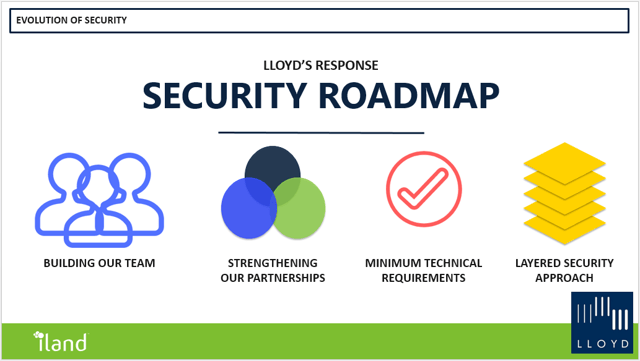
Lloyd Group’s Technology Consultant for our Financial Services community, Shaun Adams, presented on the evolution of security which broke hacking down into three main categories: Perimeter Attacks, End Point Attacks, and User Compromise. Shaun explained the background of each category and how they can affect your business, while also giving quick tips on easy ways to help combat these attacks, from making sure you have antivirus installed on personal machines to using free tools such as “haveIbeenpwned.com” to check if your email address has been compromised.
Shaun also detailed Lloyd’s approach to security, which includes investments in our internal team, strengthening our partnerships, instituting minimum technical requirements for us and our clients, and a layered security approach. The five main areas included in this approach include:
- Identify and build a strong foundation by having proper documentation and policies in place
- Protect your business with a strong network implementation, including access control, awareness training, antivirus, web and spam filtering, URL defense, and two-factor authentication
- Detect vulnerabilities with penetration tests and vulnerability scans
- Respond to attacks by utilizing a knowledgeable and responsive IT team
- Recover after an attack with appropriate backups and disaster recovery systems
Questions & Answers
Below are some highlights from our Q&A following the presentations.
When speaking about phishing attempts and wiring fund requests, isn’t that more of a personnel issue?
“Having appropriate technologies in place like antispam, web protection, and antivirus can help prevent these attacks from reaching your staff, but even the most advanced solutions don’t stop everything. This is why Lloyd advocates for the layered security approach, which includes periodic awareness training for all staff members- not just when they are hired, but ongoing. If you have 25 employees in your organization, you have 25 vulnerabilities as well.”
- Shaun Adams
How does Lloyd’s Solution Roadmap mesh with the recent NYS DFW Regulations facing Financial Institutions?
“That’s a great question! We look at all the relevant regulatory requirements, including DFS, SEC, FINRA, HIPPA, etc. when we plan out a security roadmap with our clients. A lot of the cybersecurity regulations the above agencies are looking to enforce are already considered best practices by our security team, and all are included in the layered security approach we work with our clients to develop. If you have any questions about if your firm meets the requirements, we can definitely discuss further.”
– Dave Curley


